(Optional) Application Access Policies
Create a security group to limit resources and mailboxes that Space Connect can access.
Space Connect has always used Enterprise Applications to connect to Microsoft 365 Cloud Services. Whilst this is the Microsoft recommended mechanism it has lacked the granular permissions that were possible with on-prem impersonated accounts.
Whilst impersonation did enable tighter control of accessible mailboxes it also opened the potential for numerous security loopholes and was not the recommended approach by Microsoft.
In February 2022, Microsoft announced the introduction of Application Access Policies for Enterprise Applications, bringing more granular control of mailboxes and resources.
This is an optional setup and the software will continue to work as expected if no change is made and the How to Authorise Space Connect Access has been applied. We only ever access data that is configured by you via our admin panel. This includes, but is not limited to, users, room calendars, and security groups.
Step 1:
Login to Microsoft 365 Admin and create a Mail Enabled Security group in Microsoft 365 admin and make a note of the email address assigned to the group, you will need it later.
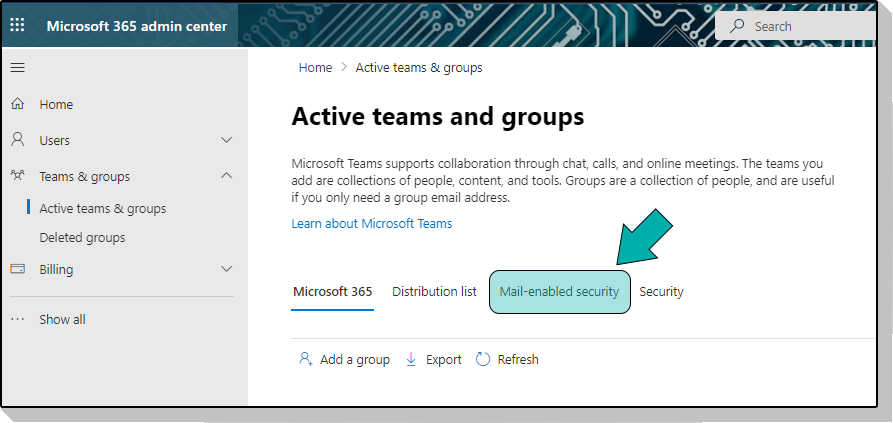
Step 2:
You will need to add all the resources that you intend to be used in Space Connect (Rooms), and the mailboxes that you want to have access to Space Connect.
Step 3:
Launch PowerShell and connect using modern authentication.
Connect-ExchangeOnline -UserPrincipalName {Microsoft 365 admin email address}
If this step does not work, then read the following guide that configures your PowerShell environment for modern authentication.
Step 4:
Apply the Application Access Policy to Space Connect Legacy Enterprise Application using the below script.
New-ApplicationAccessPolicy -AccessRight RestrictAccess -AppId "c3f87673-cff8-469e-b416-548c92def070" -PolicyScopeGroupId "mail_enabled_security_email -Description "Restrict SpaceConnect to members of Mail Enabled Security Group (mail_enabled_security_name)."
- AppId = The Space Connect Legacy Application ID
- mailenabledsecurityemail = The email address that was set up in Step 1
- Description = A description of the policy.
Step 5:
Test the newly created Application Access Policy
Test-ApplicationAccessPolicy -Identity {EmailAddressInGroup} -AppId c3f87673-cff8-469e-b416-548c92def070
An AccessCheckResult of Granted will be displayed
Test-ApplicationAccessPolicy -Identity {EmailAddressNotInGroup} -AppId c3f87673-cff8-469e-b416-548c92def070
An AccessCheckResult of Denied will be displayed.
Changes to application access policies can take longer than 1 hour to take effect in Microsoft Graph REST API calls, even when Test-ApplicationAccessPolicy shows positive results.
That's it!
The Space Connect Legacy Enterprise Application will now only be able to access the resources/mailboxes that are specified in the Mail Enabled Security group.